National Security and ESG Collide – Colonial Pipeline/JBS Attacks Change the Game
CEOs will be on the hook, Businesses remain “Aware but Unprepared”
By Jason Gold, Resolute Executive Vice President. Originally published in ESG Newsletter
“They have no idea what’s coming.”
That was the dire warning from a retired veteran of the intelligence community recently when we were discussing CEO’s and corporate board’s and the state of risk, specifically cyber, to the private sector.
In fairness, they are aware, as 71% of US CEOs said they are “extremely concerned” about cyber threats. But preparedness and a comprehensive understanding of the cyber threat, is another thing entirely, as we will see, and if ESG is going to be more than just a PR stunt, as many critics have long asserted, the moment to prove that has arrived. The Colonial Pipeline and JBS attacks on domestic economic pain points have changed the ESG game, and should re-orient all of the conversation back to its primary focus – risk.
The fact that the attacks happened was expected, possibly inevitable. But the reaction- or lack there of- from the business and investment community connecting the conversation directly to ESG reveals that, as currently constructed, ESG is in danger of being perceived as a private sector environmental awareness campaign, one to which diversity has hitched a ride.
If ESG is going to win over critics and become more widely adopted, material threat assessment has to be central to its thesis. And while climate volatility can certainly be dangerous and costly, and social issues pose a unique set of risks, cyber attacks are a substantial, material Governance risk. These risks are ever-present, expose a broad set off stakeholders, including customers, directly to harm, and in some cases are existential. (We will set aside the fact that businesses are directly funding/doing business with criminals and adverse state and terror organizations, which probably isn’t great “S”).
Now that Ransomware attacks have migrated from government targets to U.S. infrastructure supply chains, as Colonial affected our oil and gas supply and JBS affected our meat supply, it is now clear that our new battlefield is strategic stress points of our economic supply chain, which affects our National Security. And while attacks originate, in many cases, by criminal entities, they are supported, or at least protected by hostile state actors.
According to the Microsoft Digital Defense Report 2020, “cyber-attacks by the nation-states are now more in line with their political maneuvers and most of the nation-state activity originates from China, Russia, North Korea and Iran.”
Let’s look a little closer at the trends, insights and analysis of the issue.
1. Stakeholder concerns are elsewhere
It is easy to understand why all the attention is paid to the politically relevant issues of the day- the environment and social issues. ModernCISO points out four reasons why consumers aren’t focused on cyber and data breaches on a daily basis:
- Immediacy– the impact of a data breach usually doesn’t happen immediately, if at all.
- Short on Attention– life moves at a million miles an hour and endless content is raining down on everyone competing for their attention.
- Numb– with the increasing number of attacks inevitably comes eye rolls and shoulder shrugs
- Good Detection and Recovery– companies have become better at spotting fraud, especially banks, credit cards and credit services.
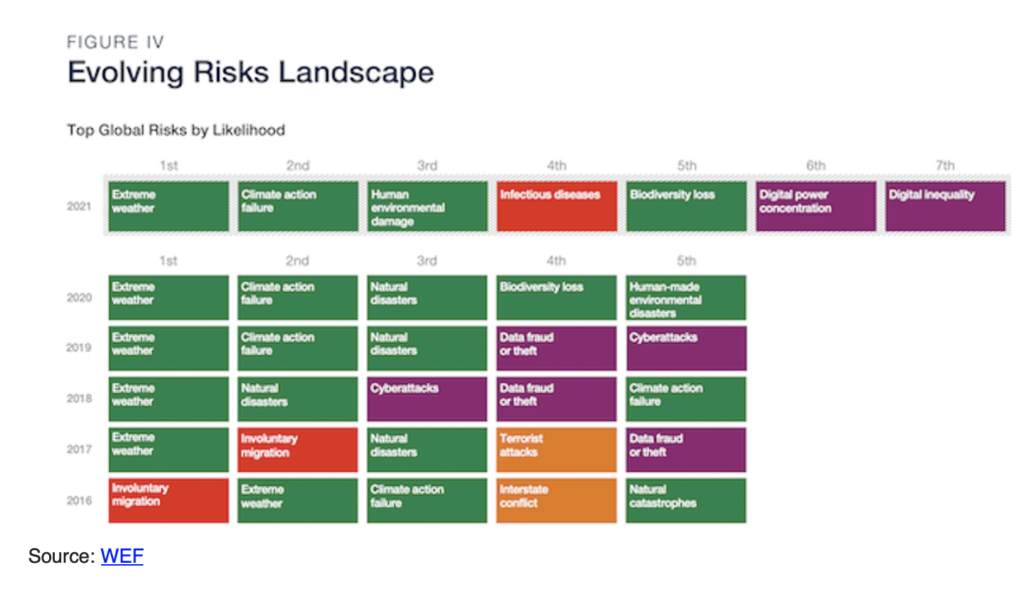
And the lackadaisical attitude is not unique to the U.S. consumer. According to the World Economic Forums “Global Risks Report 2021” survey, a collection of responses from the groups network of business, government, civil society and thought leaders, cybersecurity fell completely off the list of top concerns after 2018 (for the 2019 list).
2. CEOs are on the hook
CEO’s have a tough job, and are well compensated for it. But the level of macro-complexity facing many of them now is off the charts. Even for CEOs who run businesses that have a domestic-only footprint.
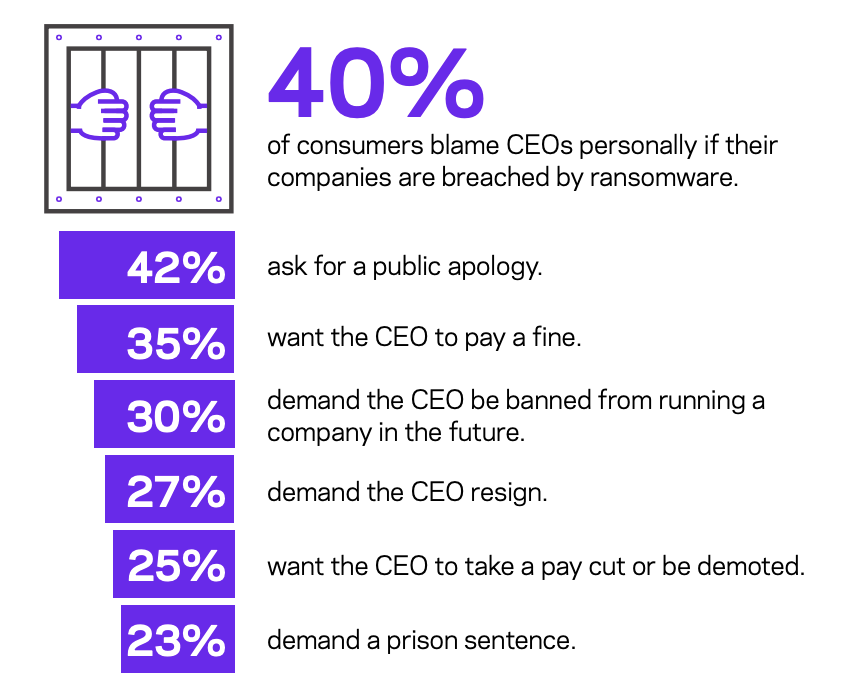
While cyber and data breaches aren’t always top of mind with consumers, they tend to blame one individual when it is- the CEO.
In an April, 2020 consumer survey commissioned by Ransomware company Veritas, those sentiments came through crystal clear:
3. BOD’s trends and expertise – Awareness Does Not Equal Preparedness
While governance issues like technology, IP, and cyber obviously have limits on transparency, companies can still send signals to the market of how serious they are in mitigating the risk of attack and how prepared they are with a comprehensive, multi-layered approach.
From the Harvard Law School Forum on Corporate Governance, only “13.8 percent of board members in the Russell 3000 (up from 10.9 percent in 2016) report having some type of technology background…” as per SEC disclosure rules. In the S&P 500 index of larger companies, 20.9 percent of corporate directors include technology expertise in their biographical profile. IT companies have, by far, the highest percentages of board members with a technology background (40.3 percent of all Russell 3000 directors at companies in the sector), followed by communication services firms (18.7 percent).”
Also of note, The average age of directors in both the Russell 3000 and S&P 500 remains unchanged, while the share of board members age 70 or older has in fact increased in the last few years.
The numbers are quite stark in an EY analysis of Fortune 100 cybersecurity disclosures:
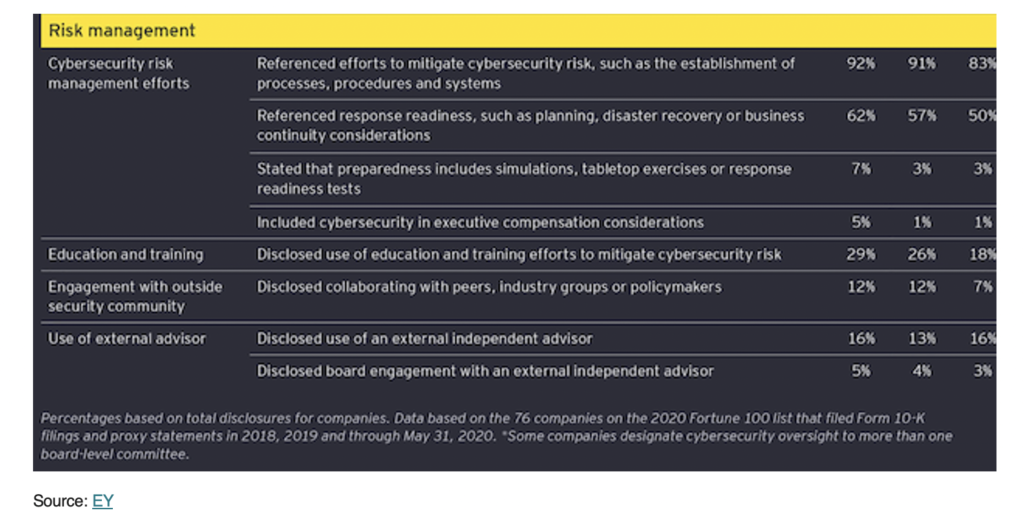
The results shows “awareness” significantly outpaces “preparedness”
So business leaders remain aware, but wholly unprepared. And according to the National Security insiders, they have no idea what’s coming.
